
Category Archives: Tech/Computers
View from my new office

Glastonbury 2013 tickets
The URL’s for tickets are as follows:
1st url:
http://glastonbury.seetickets.com
2nd url:
http://glastonbury.seetickets.com/Event/GLASTONBURY-2013-DEPOSITS/Worthy-Farm/700000
3rd url:
http://glastonbury.seetickets.com/Event/AddRegistrations (submission page?)
My views on Chip and Pin
“The new secure way to pay by card” I think it was advertised as in the early days:
The basic idea is that you have data stored on a simcard-like chip that probably holds around 64k of data. You can purchase readers for this type of card on Ebay,and software to read them is easy to come by online.The problem here is that the pin code for the card is stored on the chip with roughly 256bit encryption. So if someone copies your card they have until the card runs out to crack the code – which probably uses the same cypher for all cards as every cash machine and chip and pin device needs to be able to read the chip.
Now after reading a copy of the chip, and cracking the encryption to get the pin code, it can be copied back to an expired card ready to be used. It can even be copied to a blank smartcard as you are now asked to insert and remove the card yourself, the till operator sometimes does not even see the card. Also self checkouts at supermarkets are beginning to be widely used where there is nobody to fool, just the machine. Any transactions made this way will be verified with your pin, which only you should know according to every card issuer’s terms and conditions, and the bank will not accept responsibility for the fraud as they believe chip and pin to be secure.
Around the time chip and pin was released (DATE -14 Feb?) the 3 magic digits or card identifying digits appeared on the back of cards to allow you to use your card online securely. My issue with this is that these 3 digits are on the back of the card plain for everyone to see, so if your card is stolen or even if someone memorises or take a picture of your card then they can use your card online. Also to make a card payment over the phone to book tickets etc. you need to read the 3 magic digits to the operator at the other end of the phone to verify the transaction. Although 99% of these operators will be honest law abiding folk working in companies with strigent data confidentiality safeguards, i.e. if they write your card details down it is shredded not left on their desk for anyone to see or pick up, some won’t be. This is probably one of the many reasons that card issuers will generally accept responsibility for this type of fraud. However, that does not stop the inconvenience of being a few hundred pounds down in your account for a week or so until the money is refunded.
So what are my suggestions to secure this quite frankly mess-of-a-system?
Just follow these few simple rules:
1. Do not give anybody your card. Place your card into the chip and pin machine yourself, even if you have to hand the unit back to the operator to enter the transaction total, if they want your money they will not mind.
2. Change your pin regularly, that way you are one step ahead of the game. To remember your new pin code you could use your phone or mobile keypad which has letters against numbers to jog your memory, if you decided your word of the month was “chip” that would translate to “2447” on your keypad.
3. Obscure those magic three digits on the back of your card with a small rectangle of electrical tape or nail varnish. You can also rub the last part of the signature strip off and memorise the digits. However, I would not recommend this as beneath the signature strip is the word ‘Void’ meaning that if your card is checked by someone in a shop it may be rejected as void.
4. Do not have the same pin code for each card.
5. Have a credit card for online transactions only e.g. a credit card linked to take the full balance from your current account every month, this helps two-fold as credit cards have credit limits which you can ask to be set lower than you are offered and you have more cover for the purchases you make using a credit card. By doing this you are limiting your exposure to fraud as there will only be a limited amount of credit available to be abused and most problems should be able to be sorted before your direct debit is due to come out of your account .
If you have anything to add to my list or any comments, Get involved below..
The phone hacking scandal / technological farce?
After reports that people in the public eye have had their phones hacked, here are my ramblings on the matter from a technological view point. I am not suggesting for one minute that these claims are not true but I just question how this happened.
Most voicemail systems and answering machines have a remote access feature, which you would have to enable using the menu system and set at the very least a 4 digit pin of which there are over 10,000 combinations. The only reason I could think that someone would set this up is if they had a PA or other people who needed to access their voicemails – if this feature is not disabled by default and the pin is set to 1234 for example then it really is a security issue with the mobile provider or manufacturer that should be corrected.
Even if you have this set-up, when you dial in to your voicemail from a remote location you would be asked for your mobile number and then your pin code (or in the case of an answering machine on a landline just the pin code). If for example you have 5 new voicemails, when you have entered your details the system would say “You have 5 new messages”. The key word here is ‘new’ and not ‘saved’. If your PA had listened to your voicemails and weeded out the rubbish it would say “You have 5 saved messages”. There is a big difference here and you usually have to press a menu option to listen to them where as new messages are usually played straight away – how did people not spot this?
The remote access feature must be enabled for this to work in the first place, I know that some old answering machines had default pin codes of ‘0000’ and the remote access feature enabled by default – but this is not the case with mobile phone voicemail systems or modern answering machines.
Listening to the stories on the news I have found myself doubting the fact that someone has been able access these systems because you would need to start with the mobile number or landline number of the person, then find the mobile network operator and just brute force pin codes until one works – which you would hope would lock out after 5 or 10 tries and need resetting?
So maybe the people who carried out these attacks had a differrent approach using fake mobile base stations for a man-in-the-middle kind of attack (see hack-a-day article with vodafone singal boost boxes). However that kind of attack would involve sitting outside the home or work place of the target and waiting for them to dial the number for their voicemail and then monitoring the call – but with this sort of kit you would you not just monitor all calls? and also this sort of equipment is usually used by the government or army.
Rant over.
Epic win
Bloom Box
The Bloom box is a small power plant (or large fuel cell) that can run on Natural gas & BioGas please have a look at the video from Engadget below:
Timelapse & Mix
A timelapse me and sarge put together.
Bumptop 3D Desktop
I got my hands on a beta of this a while back when I had a touch screen to test it on but they have a full release now:
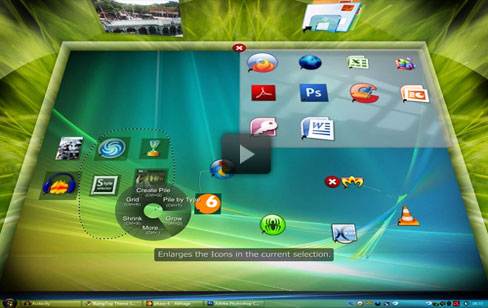
You can make piles of files and arrange by keyword in to piles, you can put photos and notes on the walls, simply throw a picture at the Facebook icon to upload. (full feature list)
Video:
You can download Bumptop here: http://bumptop.com/ (There is a free feature limited version, Pro is about £18)
I hope they release a linux version of Bumptop as it would be a good addition to compiz.
What is the Beebotron?
Again another site I found while searching around!
This site provides, amongst other things, rtsp RealAudio .ra and .rm streaming links for BBC Listen Again programs that the you may prefer to listen to (or Listen Again to) from here rather than using the BBC iPlayer. It will let you listen to BBC radio broadcasts on smartphones, Pocket PCs, PDAs, and other mobile devices. It also works on PCs, Macs and pretty much anything else that supports RealAudio, WMA, or Flash.
Very useful 🙂

